JWT vs. Session Authentication
Authentication is a critical component of web applications, and two popular approaches are JWT-based authentication and traditional session-based authentication. This guide compares these two methods, highlighting their differences, advantages, disadvantages, and appropriate use cases.
Overview of Authentication Methods
Session-Based Authentication
Traditional authentication method where the server maintains session state and issues a session ID to the client, typically stored in a cookie.
JWT-Based Authentication
Modern authentication method where the server issues a signed token containing user information, which the client includes in subsequent requests.
How They Work
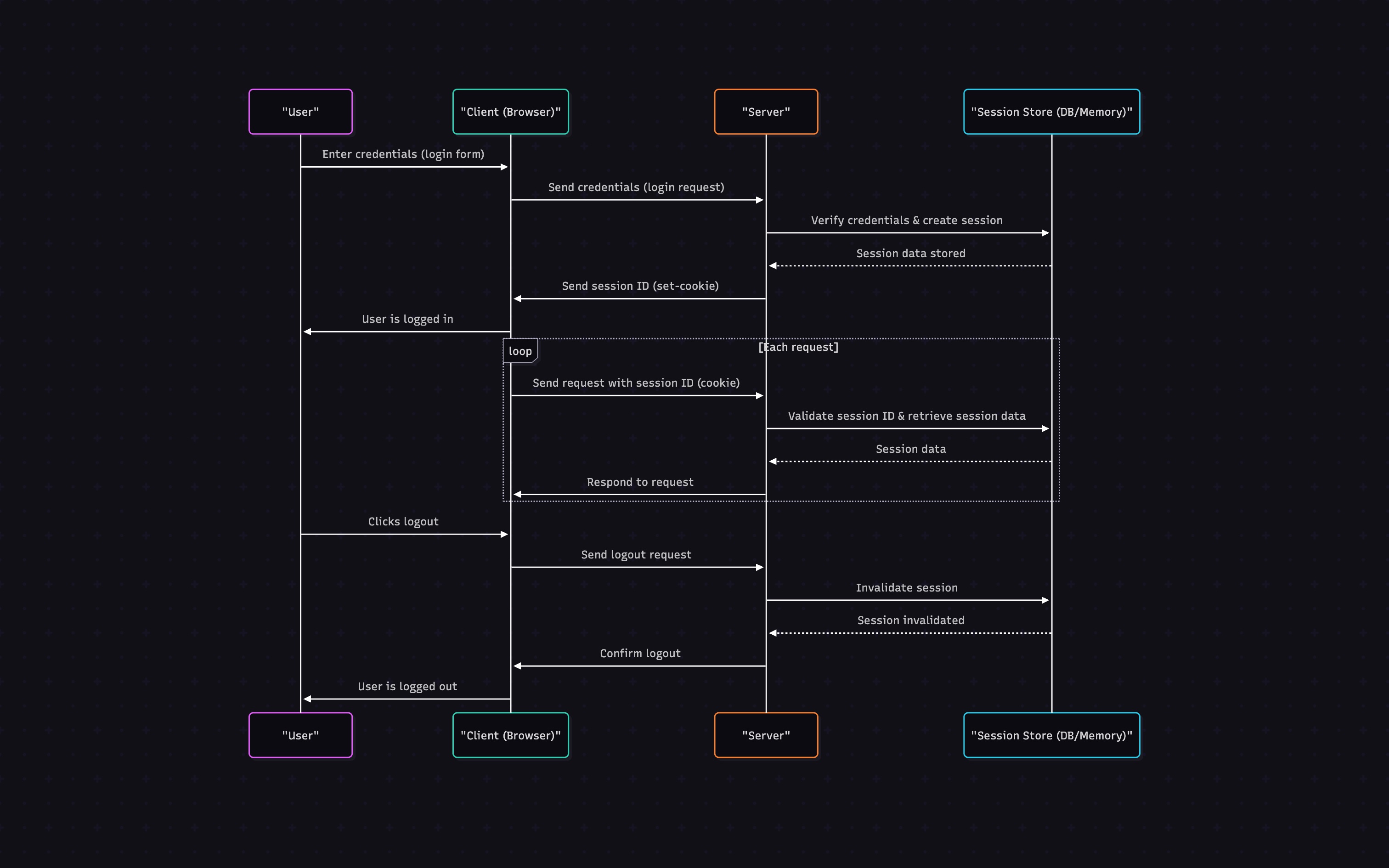
Session-Based Authentication
- User logs in with credentials
- Server verifies credentials and creates a session
- Server stores session data in memory or database
- Server sends a session ID to the client (usually in a cookie)
- Client includes the session ID in subsequent requests
- Server validates the session ID and retrieves session data
- When user logs out, server invalidates the session
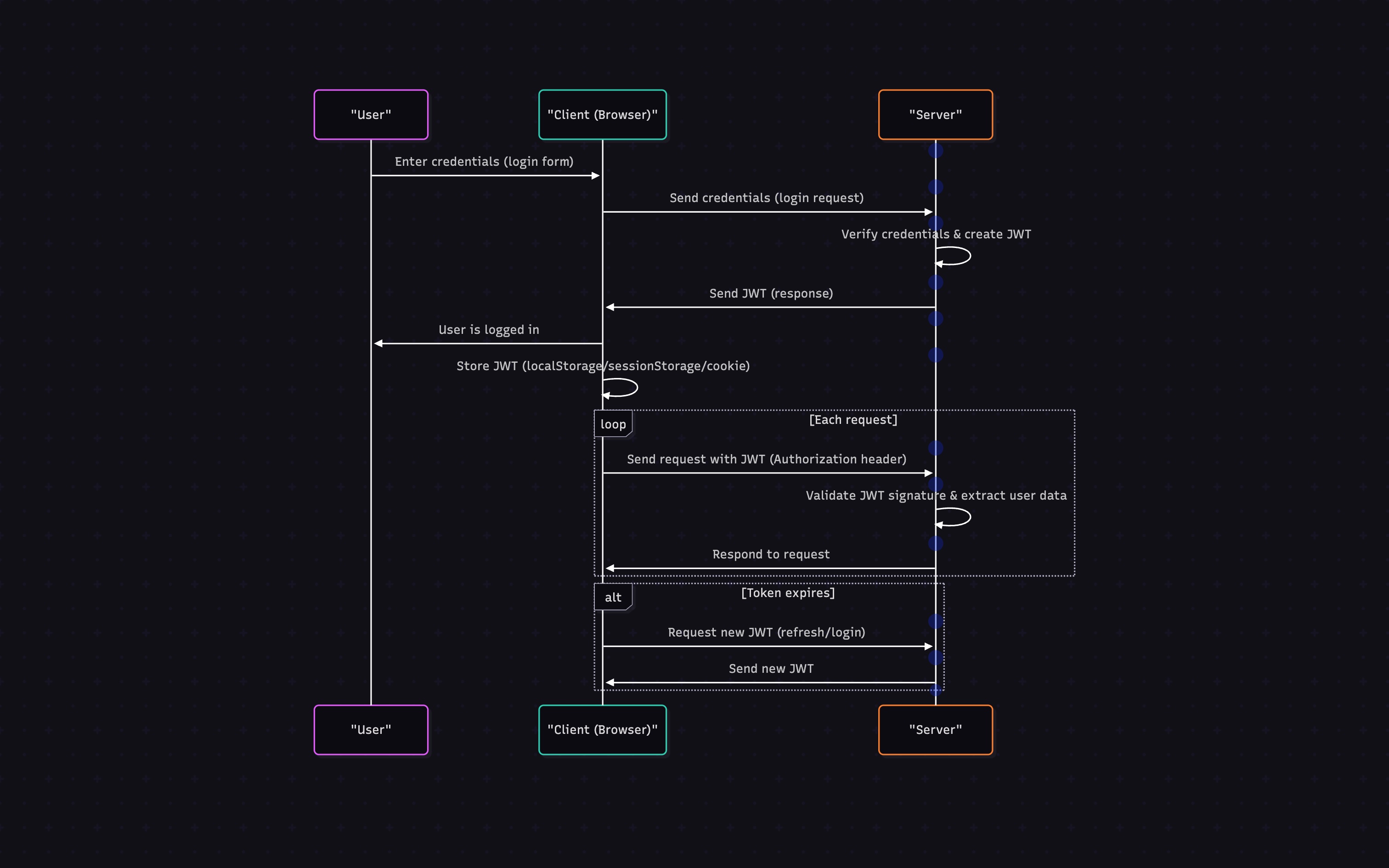
JWT-Based Authentication
- User logs in with credentials
- Server verifies credentials and creates a JWT
- JWT contains encoded user data and is signed by the server
- Server sends the JWT to the client
- Client stores the JWT (localStorage, sessionStorage, or cookie)
- Client includes the JWT in subsequent requests (Authorization header)
- Server validates the JWT signature and extracts user data
- When token expires, client needs to request a new one
Key Differences
| Feature | Session-Based Auth | JWT-Based Auth |
|---|---|---|
| State Management | Stateful (server stores session data) | Stateless (server doesn't store token data) |
| Storage Location | Server-side (database, cache, memory) | Client-side (token contains all necessary data) |
| Scalability | Requires session synchronization across servers | Easily scalable (no server-side state) |
| Token Size | Small (just a reference ID) | Larger (contains encoded user data) |
| Security | Session ID is opaque (no data exposure) | Payload is encoded but not encrypted (potential data exposure) |
| Revocation | Easy (delete session from server) | Difficult (requires blacklist or short expiration) |
| Cross-Domain | Challenging (CORS issues with cookies) | Easier (can be sent in Authorization header) |
| Mobile/IoT Support | Less suitable (cookie management issues) | Well-suited (easy to include in headers) |
Advantages and Disadvantages
Session-Based Authentication
Advantages
- Complete control over sessions (can invalidate at any time)
- Smaller payload size (only sends session ID)
- Session data can be changed without affecting the client
- More secure for sensitive operations (no data exposure)
- Well-established, mature approach
Disadvantages
- Requires server-side storage (memory, database)
- Scaling challenges (session synchronization across servers)
- CORS complications with cookies
- Less suitable for modern architectures (microservices, serverless)
- Session management overhead
JWT-Based Authentication
Advantages
- Stateless (no server-side storage required)
- Highly scalable (works well with distributed systems)
- Cross-domain friendly (easy to use with multiple services)
- Contains user data (reduces database lookups)
- Well-suited for modern architectures (microservices, APIs)
- Works well for mobile and IoT applications
Disadvantages
- Difficult to invalidate tokens before expiration
- Payload size can become large
- Data in token cannot be changed until new token is issued
- Potential security risks if not implemented correctly
- Payload data is visible (though encoded) to the client
When to Use Each Approach
Use Session-Based Authentication When:
- You need absolute control over user sessions
- Your application handles highly sensitive data
- You need to store complex session state
- You have a monolithic application architecture
- You need to track user activity closely
- Immediate session invalidation is a requirement
Use JWT-Based Authentication When:
- You're building stateless, scalable services
- You have a microservices architecture
- You need cross-domain authentication
- You're developing mobile or IoT applications
- You want to reduce database lookups
- You need to pass authentication between different services
Best Practices
Session-Based Authentication Best Practices
- Use secure, HttpOnly, and SameSite cookies
- Implement CSRF protection
- Generate strong, random session IDs
- Set appropriate session timeouts
- Implement session rotation on privilege changes
- Use a reliable session store (Redis, database)
- Provide session invalidation on logout
JWT-Based Authentication Best Practices
- Keep tokens short-lived (15-30 minutes)
- Implement refresh token rotation
- Use strong signing algorithms (RS256, ES256)
- Include only necessary claims in the payload
- Validate tokens properly on the server
- Store tokens securely on the client
- Implement a token blacklist for critical invalidations
- Always use HTTPS for token transmission
Hybrid Approaches
Many modern applications use hybrid approaches that combine the benefits of both methods:
JWT with Server-Side Storage
Use JWTs but also maintain a reference to them on the server, allowing for explicit invalidation while still benefiting from the JWT's self-contained nature.
Short-Lived JWTs with Refresh Tokens
Use short-lived JWTs (access tokens) for API access, combined with longer-lived refresh tokens that are stored server-side and can be invalidated.
Tip: The refresh token approach provides a good balance between the statelessness of JWTs and the control of session-based authentication.
Conclusion
Both session-based and JWT-based authentication have their place in modern web development. The choice between them depends on your specific application requirements, architecture, and security needs.
For many applications, a hybrid approach using short-lived JWTs with server-side refresh tokens provides the best balance of security, scalability, and control.